WhatsApp is one of the world’s most widely used messaging apps, praised for its end-to-end encryption that ensures messages remain private between sender and receiver. But how does this encryption actually work under the hood? The core cryptographic process behind WhatsApp’s secure messaging is the Diffie-Hellman key exchange—a brilliant method that enables two parties to generate a shared secret over an insecure channel. Here’s a detailed, SEO-optimized explanation of how the Diffie-Hellman exchange works in WhatsApp and why it’s critical for your privacy.
What is Diffie-Hellman Key Exchange?
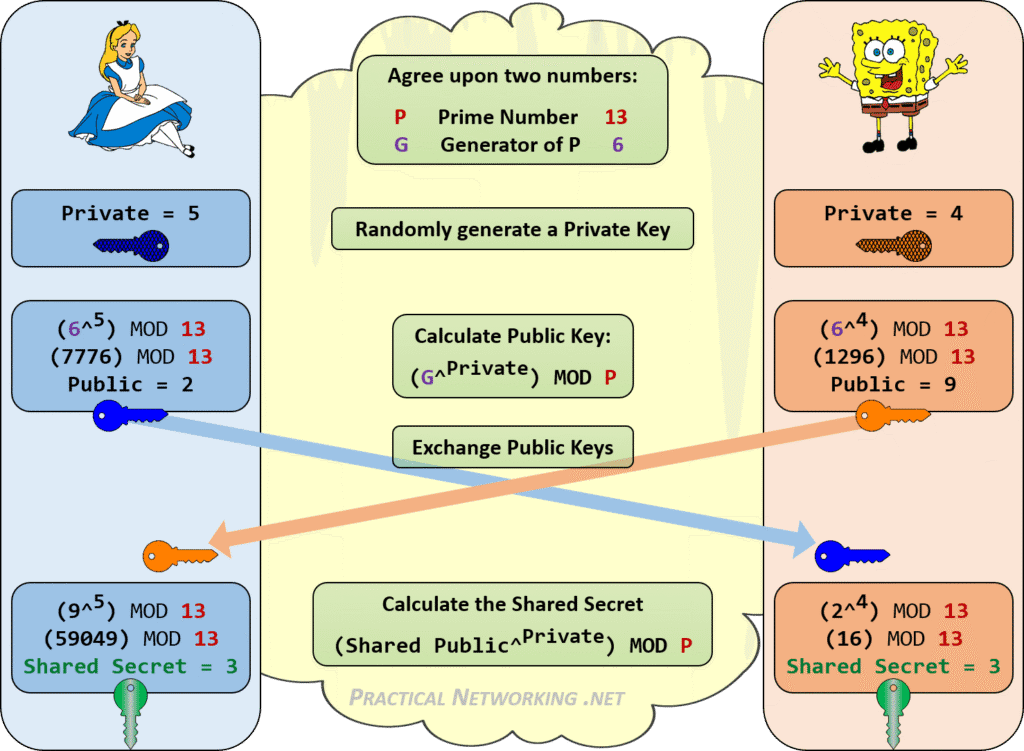
The Diffie-Hellman key exchange, developed in 1976 by Whitfield Diffie, Martin Hellman, and Ralph Merkle, is a method that enables two parties—let’s call them Alice and Bob—to create a shared secret key without transmitting it directly. This is essential for secure communication, as it prevents eavesdroppers, such as Eve, from easily determining the key.
To illustrate, consider a simple analogy: Alice and Bob each have a secret color (Alice has red, Bob has cyan) and agree on a public color, yellow. Alice mixes red with yellow to create orange and sends it to Bob. Bob mixes cyan with yellow to create green and sends it to Alice. Alice then mixes Bob’s green with her red to get yellow-brown, and Bob mixes Alice’s orange with his cyan to also get yellow-brown. They now share the same secret color, yellow-brown, without ever revealing their secret colors.
Mathematically, Alice and Bob agree on a large prime number ( p ) and a generator ( g ). Alice selects a secret number ( a ), computes ( A = g^a \mod p ), and sends ( A ) to Bob. Bob selects a secret number ( b ), computes ( B = g^b \mod p ), and sends ( B ) to Alice. Alice computes the shared secret ( s = B^a \mod p ), and Bob computes ( s = A^b \mod p ). Since ( B^a = (g^b)^a = g^{ba} \mod p ) and ( A^b = (g^a)^b = g^{ab} \mod p ), both arrive at the same shared secret ( s = g^{ab} \mod p ).
For example, with ( p = 23 ) and ( g = 5 ):
| Step | Alice’s Action | Bob’s Action | Shared Secret |
|---|---|---|---|
| 1 | Chooses ( a=4 ), sends ( A = 5^4 \mod 23 = 4 ) | Chooses ( b=3 ), sends ( B = 5^3 \mod 23 = 10 ) | – |
| 2 | Computes ( s = 10^4 \mod 23 = 18 ) | Computes ( s = 4^3 \mod 23 = 18 ) | ( s=18 ) |
This shared secret can then be used to encrypt subsequent communications using a symmetric key cipher.
Elliptic Curve Diffie-Hellman (ECDH)
While the traditional Diffie-Hellman exchange is effective, it requires large numbers to ensure security, which can be computationally intensive. WhatsApp uses a more efficient variant called Elliptic Curve Diffie-Hellman (ECDH), which leverages elliptic curve cryptography. ECDH achieves equivalent security with smaller key sizes, making it ideal for mobile devices with limited processing power.
In ECDH, the protocol operates on points on an elliptic curve rather than large integers modulo a prime. The mathematical details are complex, but the core idea remains: two parties exchange public points on the curve, and each uses their private key to compute a shared secret point. WhatsApp employs the Curve25519 elliptic curve, which is designed for ECDH, offering 128 bits of security with a 256-bit key size. Curve25519 is known for its speed, security, and lack of known patents, making it a preferred choice for cryptographic applications (Signal Protocol).
X3DH in WhatsApp
WhatsApp’s end-to-end encryption is powered by the Signal Protocol, developed by Open Whisper Systems (now Signal Technology Foundation). The Signal Protocol uses an advanced form of Diffie-Hellman called Extended Triple Diffie-Hellman (X3DH) for initial key agreement. X3DH is tailored for asynchronous communication, allowing users to establish a secure connection even if they are not online simultaneously, which is critical for a messaging app like WhatsApp.
In X3DH, each user maintains several key pairs:
- Identity Key Pair: A long-term key pair used for authentication.
- Signed Prekey Pair: A key pair that is periodically refreshed and signed with the identity key to ensure authenticity.
- One-Time Prekeys: A set of key pairs used only once and then discarded to enhance security.
When Alice wants to send a message to Bob, she retrieves Bob’s identity key, signed prekey, and a one-time prekey (if available) from the WhatsApp server. She then performs three or four Diffie-Hellman operations:
- Between her identity key and Bob’s signed prekey.
- Between her ephemeral key (generated for this session) and Bob’s signed prekey.
- Between her ephemeral key and Bob’s identity key.
- (Optional) Between her ephemeral key and Bob’s one-time prekey.
These operations produce results that are combined to create a master secret, which initializes the Double Ratchet algorithm for ongoing secure communication (X3DH Specification).
Double Ratchet Algorithm
After the initial key exchange via X3DH, WhatsApp uses the Double Ratchet algorithm to manage session keys for continuous communication. The Double Ratchet combines two mechanisms:
- Diffie-Hellman Ratchet: Periodically derives new root keys using Diffie-Hellman exchanges.
- Symmetric Ratchet: Derives new chain keys from the root keys for each message.
This dual-ratchet system ensures that each message is encrypted with a unique key, providing forward secrecy. Forward secrecy means that even if an attacker compromises a user’s device and obtains their private keys, they cannot decrypt past messages, as those messages were encrypted with keys that have been ratcheted forward and discarded (Signal Protocol).
Security and Authentication
The Diffie-Hellman key exchange itself does not provide authentication, meaning it is vulnerable to man-in-the-middle attacks without additional measures. WhatsApp addresses this through the Signal Protocol’s use of signed prekeys and identity keys. The signed prekey is signed with the user’s identity key, allowing the recipient to verify its authenticity. Additionally, WhatsApp offers a feature where users to verify each other’s identity keys by comparing a fingerprint, ensuring they are communicating with the intended party and not an impostor.
The use of one-time prekeys further enhances security by limiting the impact of a compromised prekey. If a one-time prekey is used, it is discarded after the session, reducing the window of vulnerability. The Curve25519 implementation also protects against known cryptographic attacks, such as the Logjam attack, by using a strong key size and modern cryptographic practices (Diffie-Hellman Overview).
Practical Implications
The integration of Diffie-Hellman, specifically ECDH and X3DH, into WhatsApp’s Signal Protocol provides several key benefits:
- Confidentiality: Messages are only readable by the intended recipient.
- Forward Secrecy: Past messages remain secure even if keys are compromised.
- Authentication: Signed prekeys and identity keys verify user identities.
- Efficiency: Curve25519 and ECDH ensure fast performance on mobile devices.
This robust implementation has made WhatsApp a trusted platform for secure communication, protecting billions of messages daily. However, it’s worth noting that while the encryption is strong, user trust also depends on WhatsApp’s server practices for key distribution and the broader security of the user’s devices themselves.
How WhatsApp Implements Diffie-Hellman?
WhatsApp, owned by Meta, uses the Signal Protocol, which is based on an extended version of the Elliptic Curve Diffie-Hellman (ECDH) algorithm. Here’s how the key exchange process works in WhatsApp:
1. Each User Has a Key Pair
- When you install WhatsApp, it generates a private and a public key.
- The private key is stored securely on your device.
- The public key is shared with WhatsApp servers so others can retrieve it when starting a chat.
2. Initiating the Key Exchange
- When User A wants to send a message to User B, WhatsApp retrieves User B’s public key from the server.
- User A combines their private key with User B’s public key using the ECDH algorithm to create a shared secret key.
3. Only the Intended Devices Can Decrypt Messages
- This shared secret key is used to encrypt the message.
- When User B receives it, their device uses their private key and User A’s public key to derive the same shared key and decrypt the message.
4. Forward Secrecy
- For each message, WhatsApp also uses ephemeral session keys (temporary keys that change frequently), adding another layer of protection known as perfect forward secrecy.
- Even if someone somehow gets your private key later, they can’t decrypt past conversations.
An Easy Example with Lock and Box (Physical Analogy)
Say, You want to send your friend a box with a key inside, but you don’t trust the mail — someone might open it!
Step-by-step:
- You put a key in a box, lock it with your padlock, and send it to your friend.
- Your friend gets the box, can’t open it — so they add their own padlock (now 2 locks), and send it back to you.
- You remove your padlock, leaving just your friend’s padlock, and send it again.
- Now your friend removes their padlock — and finally opens the box to get the key.
Only you and your friend could unlock it because you both had the right padlocks (private secrets).
What Diffie-Hellman does in WhatsApp?
| Feature | What DH helps with |
|---|---|
| Secure Key Exchange | Generates a shared secret over public network |
| End-to-End Encryption | Ensures only sender & receiver can read data |
| Forward Secrecy | Old messages stay safe even if one key is stolen |
| Perfect Secrecy | Secret never sent directly |
Why Diffie-Hellman Is Secure in WhatsApp?
- No key transmission: The secret key is never sent—only derived independently.
- End-to-end encryption: Only the sender and receiver can read the message.
- Tamper detection: WhatsApp includes safety codes so users can verify if communication is secure.
- Forward secrecy: Keys change frequently, limiting data exposure even in case of a breach.
Final Thoughts
The Diffie-Hellman key exchange in WhatsApp is a foundational security mechanism enabling true end-to-end encryption. By generating shared secret keys without actually transmitting them, WhatsApp ensures that even if messages travel through public networks, no third party—including WhatsApp itself—can read them. This system, backed by the Signal Protocol and enhanced with ECDH and forward secrecy, makes WhatsApp one of the most secure messaging platforms available today.
Frequently Asked Questions
How does WhatsApp store private keys?
WhatsApp stores private keys securely on the user’s device, not on its servers. Each user’s encryption keys are generated and managed locally to enable end-to-end encryption. This means only the sender and receiver can read the messages—not even WhatsApp has access to the content. The private keys are stored in a protected area of the device’s operating system using security features like Android Keystore or Apple’s Secure Enclave, which help prevent unauthorized access or extraction. This local key storage is critical to maintaining WhatsApp’s commitment to user privacy and message security.
Which algorithm does WhatsApp use?
WhatsApp uses the Signal Protocol for end-to-end encryption, which is a highly secure cryptographic algorithm developed by Open Whisper Systems. This protocol combines several algorithms to ensure privacy and security, including the Double Ratchet Algorithm, X3DH key agreement protocol, and AES-256 for encryption, along with HMAC-SHA256 for message authentication. Together, these algorithms provide features like forward secrecy and asynchronous messaging, ensuring that messages cannot be decrypted even if keys are compromised later. This robust cryptographic approach makes WhatsApp’s communication secure and trusted by billions of users worldwide.
Which protocol does WhatsApp use?
WhatsApp uses the Signal Protocol as its core encryption protocol to ensure end-to-end security for messages, calls, photos, and videos. Developed by Open Whisper Systems, the Signal Protocol is a modern, open-source cryptographic protocol that combines the Double Ratchet algorithm, X3DH (Extended Triple Diffie-Hellman) for key exchange, and AES-256 encryption for data confidentiality. This protocol enables features like forward secrecy, asynchronous messaging, and perfect message confidentiality, meaning only the sender and recipient can read the content—even WhatsApp cannot access it.
Does WhatsApp use HTTP or WebSocket?
WhatsApp primarily uses custom-built protocols over TCP and WebSocket-like persistent connections for real-time communication, rather than standard HTTP. While HTTP may be used for tasks like media upload or initial authentication, the core messaging functionality relies on a persistent connection to WhatsApp’s servers, allowing for instant message delivery, presence updates, and synchronization. This real-time communication is more efficiently handled through a WebSocket-style protocol, which maintains an open connection, reducing latency and improving responsiveness for users across mobile networks.
In what applications is the Diffie-Hellman key exchange used?
The Diffie-Hellman key exchange is widely used in applications that require secure key generation and exchange over an insecure channel. It is a foundational component in VPNs (like IPsec), TLS/SSL protocols for secure websites, encrypted messaging apps such as Signal and WhatsApp, and secure email systems like PGP. In these applications, Diffie-Hellman enables two parties to establish a shared secret key without transmitting the key itself, which can then be used for symmetric encryption. Its ability to securely initiate communication makes it essential in modern cryptographic systems.
What encryption does Telegram use?
Telegram uses a custom encryption protocol called MTProto to secure its communications. For cloud chats (regular chats), Telegram uses server-client encryption, where messages are encrypted between the user and Telegram’s servers using AES-256 symmetric encryption, RSA-2048 asymmetric encryption, and Diffie-Hellman key exchange. However, only Secret Chats in Telegram are truly end-to-end encrypted, meaning only the sender and receiver can read the messages. These Secret Chats also use MTProto but operate exclusively on the users’ devices, ensuring no server access to the content.
What encryption does Signal use?
Signal uses the Signal Protocol, one of the most secure end-to-end encryption protocols available. It combines several advanced cryptographic algorithms, including AES-256 for symmetric encryption, Curve25519 for key exchange, and HMAC-SHA256 for message authentication. Signal also uses the Double Ratchet Algorithm and X3DH (Extended Triple Diffie-Hellman) to ensure forward secrecy and asynchronous messaging, meaning even if a session key is compromised, past messages remain secure. This protocol protects all forms of communication—texts, voice, video, and file transfers—ensuring that only the sender and recipient can read or access the data.
Which is safer, WhatsApp or Telegram?
WhatsApp is generally considered safer than Telegram when it comes to message privacy, primarily because it uses end-to-end encryption (E2EE) by default for all chats, calls, and media, powered by the highly secure Signal Protocol. This means only the sender and receiver can access the content, and not even WhatsApp can read messages. In contrast, Telegram only offers E2EE in its “Secret Chats”, while regular chats are encrypted between the client and server, allowing Telegram to access message content. Therefore, for users prioritizing privacy and message confidentiality, WhatsApp provides stronger default encryption protections.