Hackers steal personal data from our devices through various methods, including phishing scams, malware, and fake Wi-Fi networks. Phishing involves hackers posing as legitimate entities to trick users into revealing sensitive information, such as passwords.
This can be done through fake login pages or deceptive emails and messages. Malware is another common tool used by hackers, where malicious software is downloaded onto a device to steal personal information. Additionally, hackers may set up fake Wi-Fi networks to redirect users to malicious websites and capture their data.
It is important to understand these methods and take precautions to protect personal data from being stolen by hackers.
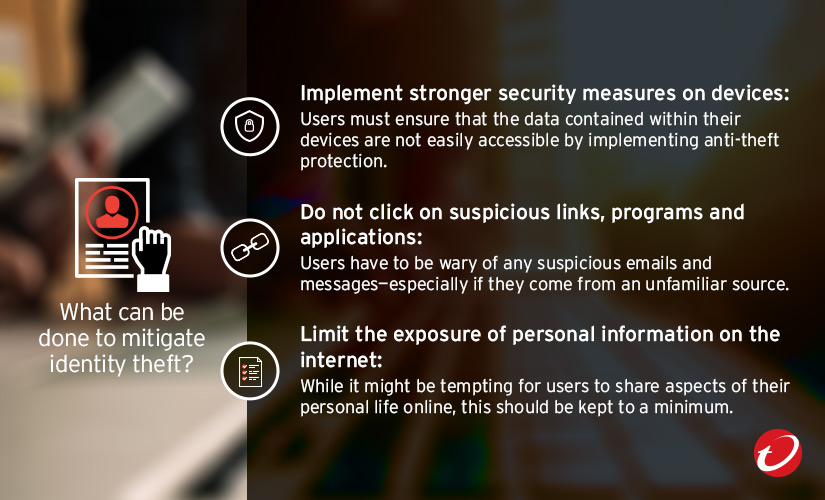
Credit: www.trendmicro.com
Understanding Personal Data Vulnerability
In this digital era, our personal data has become increasingly vulnerable to hackers and cybercriminals. Understanding how hackers steal personal data from our devices is crucial to protect ourselves from falling victim to their malicious activities. By recognizing the types of personal data targeted by hackers and the significance of digital footprints in data vulnerability, we can take proactive steps to secure our information and maintain our online privacy.
When it comes to stealing personal data, hackers have a wide range of information they target. By obtaining different types of personal data, they can carry out identity theft, financial fraud, and various other illegal activities. Here are some common types of personal data targeted by hackers:
- Social Security Numbers (SSN)
- Credit Card Information
- Bank Account Details
- Email Addresses
- Passwords
- Health Records
- Personal Identifiable Information (PII)
By gaining access to any of these personal data types, hackers can exploit the information for their benefit, causing significant damage to individuals and organizations alike.
Our digital footprints play a critical role in our data vulnerability. Every online activity we engage in leaves a trace, forming a digital footprint that hackers can exploit. Here are some instances where digital footprints can make us vulnerable:
- Sharing Personal Information on Social Media Platforms
- Using Weak and Repeated Passwords
- Clicking on Suspicious Links or Downloading Malicious Attachments
- Transmitting Unencrypted Data over Unsecured Wi-Fi Networks
These actions can increase the risk of our personal information falling into the wrong hands, making it easier for hackers to steal our data.
By understanding the various types of personal data targeted by hackers and the role digital footprints play in our vulnerability, we can take proactive steps to protect ourselves. Implementing strong security measures, such as using complex passwords, enabling two-factor authentication, and being cautious of the information we share online, can significantly reduce the risk of personal data theft.
Tactics Hackers Use For Data Breach
Hackers use various tactics to steal personal data from our devices, such as phishing scams where they impersonate legitimate entities to collect sensitive information like passwords. They may also employ malware, fake Wi-Fi networks, and other methods to gain access to our devices and steal personal information.
The Role Of Phishing In Data Extraction
One of the most cunning tactics hackers use to breach our personal data is through phishing attacks. Phishing occurs when hackers impersonate trustworthy entities and deceive users into providing sensitive information, such as passwords or credit card numbers.
Utilizing various methods like email, SMS, or even social media messages, hackers create convincing scenarios that prompt users to click on malicious links or provide their personal information. These phishing attacks can also involve the use of spoofed websites, which are fake replicas of legitimate sites that trick users into entering their login credentials.
Once the hacker has obtained these sensitive details, they gain unauthorized access to our personal accounts and acquire valuable data that can be exploited for identity theft, financial fraud, or other malicious activities. Therefore, it is crucial to remain vigilant and always verify the authenticity of communication and websites before sharing any personal information.
Malware And Its Variants As Data Theft Tools
Malware, short for malicious software, is another common tool employed by hackers to steal personal data from our devices. Malware comes in various forms, including viruses, trojans, ransomware, and spyware. These malicious programs can infiltrate our devices through different means, such as downloading infected attachments, clicking on suspicious links, or visiting compromised websites.
Once installed on our devices, malware can collect sensitive information such as login credentials, credit card details, and even monitor our online activities without our knowledge. It can record keystrokes, capture screenshots, and even hijack our webcams, posing a severe risk to our privacy and security.
To protect ourselves from malware, it is crucial to have robust antivirus software installed on our devices, regularly update our operating systems and applications, and exercise caution when downloading files or clicking on links from unknown or unverified sources.
How Keyloggers Capture Sensitive User Inputs
Keyloggers are a type of software or hardware that hackers employ to record every keystroke made on our devices. By capturing these keystrokes, keyloggers can obtain vital information such as usernames, passwords, credit card details, and other sensitive user inputs.
Hackers can distribute keyloggers through various means, including email attachments, fake software downloads, or even physical access to our devices. Once installed, keyloggers silently run in the background, recording our every keystroke and sending the obtained data to the hackers.
Protecting ourselves against keyloggers involves taking precautions such as avoiding suspicious downloads, regularly scanning our devices for malware, and using anti-keylogging software to detect and prevent these malicious programs from operating on our devices.
Exploiting Unsecured Networks For Data Interception
Hackers are known to prey on the vulnerabilities of unsecured networks to intercept data transmitted between our devices and the internet. These unsecured networks, often found in public places like cafes, airports, or hotels, lack encryption protocols and easily allow hackers to eavesdrop on our online activities.
By setting up fake public Wi-Fi networks or using other techniques like man-in-the-middle attacks, hackers can intercept our sensitive information, including passwords, credit card details, and personal communications. They can use this information for identity theft, financial fraud, or further data breaches.
To mitigate the risk of data interception, it is crucial to exercise caution while connecting to public Wi-Fi networks. Always verify the network’s authenticity with the staff if possible, and utilize a virtual private network (VPN) for encrypted connections, ensuring that our data remains secure and private even on unsecured networks.
Stealthy Infiltrations And System Gaps
When it comes to stealing personal data from our devices, hackers employ various techniques, including stealthy infiltrations and exploiting system gaps. These methods allow them to gain unauthorized access to our devices and extract sensitive information without our knowledge.
Recognizing Signs Of Compromised Device Security
It is crucial to be aware of the signs indicating compromised device security to detect any potential threats. Some common signs include:
- Unusual or unauthorized activity on your device
- Unexpected changes in system settings
- Slow device performance or frequent crashes
- Unknown applications or files appearing on your device
- Unusual network traffic or data usage
If you notice any of these signs, it is essential to take immediate action to protect your personal data.
Software Vulnerabilities And Outdated System Risks
Software vulnerabilities and outdated systems pose significant risks to device security. Hackers often exploit known vulnerabilities in software or operating systems to gain unauthorized access. This is why it is crucial to regularly update your software and operating system, as updates often include patches and fixes for these vulnerabilities.
Additionally, using outdated software or unsupported operating systems increases the risk of being targeted by hackers. Unsupported systems no longer receive security updates, making them prime targets for hackers seeking to exploit known vulnerabilities.
By keeping your software and operating system up to date, you can minimize the risk of falling victim to attacks that exploit software vulnerabilities.
The Impact Of Social Engineering On Device Defenses
Social engineering plays a significant role in compromising device defenses. Hackers often use psychological manipulation to deceive individuals into disclosing sensitive information or granting them unauthorized access.
- Phishing: Sending fraudulent emails or messages that appear to be from trusted sources, tricking users into revealing their credentials or clicking malicious links.
- Baiting: Leaving physical or digital “bait” that entices users to take specific actions, such as inserting infected USB drives or downloading compromised files.
- Pretexting: Creating a false pretense or scenario to gain the trust of individuals and extract sensitive information.
It is important to be cautious and skeptical of unsolicited requests for personal information, even if they seem legitimate. By staying vigilant and having a good understanding of social engineering tactics, you can enhance your device’s defenses against such attacks.
Device Security Evasion Techniques
In the ever-evolving landscape of cyber threats, hackers are becoming increasingly sophisticated in their methods of stealing personal data from our devices. They employ various techniques to bypass device security measures, exploiting vulnerabilities to gain unauthorized access to sensitive information. Understanding these techniques is crucial in order to better protect ourselves from potential data breaches.
Rooting And Jailbreaking: Doorways To Data Exploitation
The first technique hackers utilize to evade device security is through rooting and jailbreaking. Rooting refers to gaining administrative access to an Android device, while jailbreaking is the process of removing software restrictions on an iPhone. By gaining root or jailbreak access, hackers can easily bypass security mechanisms and gain complete control over the device, opening the door to data exploitation.
The Use Of Trojans And Backdoor Entries
Another technique employed by hackers is the use of Trojans and backdoor entries. Trojans are malicious software that disguise themselves as legitimate applications, tricking users into downloading and installing them. Once installed, these Trojans create a backdoor entry point, allowing hackers to remotely access the device and steal personal data without the user’s knowledge.
Man-in-the-middle Attacks And Encryption Circumvention
One of the most sophisticated techniques used by hackers is the man-in-the-middle attack and encryption circumvention. In a man-in-the-middle attack, hackers intercept communication between two parties, allowing them to eavesdrop, manipulate, or steal sensitive information exchanged between the two. Encryption circumvention involves bypassing encryption protocols, allowing hackers to access encrypted data and decrypt it to obtain the original information.
While these techniques may seem complex, it’s important to be aware of them in order to adequately protect our devices and personal data. By understanding the strategies hackers employ to evade device security, we can actively implement measures to strengthen our defenses and safeguard our sensitive information.
Proactive Data Protection Steps
In today’s digital era, where hackers are constantly evolving their techniques to steal personal data from our devices, it is crucial to implement proactive data protection steps. By taking these measures, you can significantly reduce the risk of falling victim to cyber-attacks and safeguard your sensitive information. In this article, we will discuss three important steps you can take for proactive data protection: Importance of regular software updates and patches, Implementing multi-factor authentication (MFA), and Advantages of using VPNs for secure connections.
Importance Of Regular Software Updates And Patches:
Regular software updates and patches play a critical role in maintaining the security of your devices. Software vulnerabilities are often targeted by hackers to gain unauthorized access to your personal data. By keeping your operating system, browsers, and other software up to date, you ensure that any known security flaws are patched, making it harder for hackers to exploit them.
Implementing Multi-factor Authentication (mfa):
Multi-factor authentication (MFA) adds an extra layer of security to your accounts by requiring multiple forms of verification. Typically, this involves something you know (such as a password), something you have (like a unique code sent to your phone), or something you are (such as a fingerprint or facial recognition). By enabling MFA, even if a hacker manages to obtain your password, they will still need access to your secondary verification method, making it significantly more difficult for them to compromise your accounts.
Advantages Of Using VPNs For Secure Connections:
Virtual Private Networks (VPNs) provide a secure and private connection between your device and the internet. By encrypting your traffic and routing it through a server in a different location, VPNs protect your online activities from prying eyes. This is especially important when using public Wi-Fi networks, which are often targeted by hackers. VPNs not only secure your data but also hide your IP address, making it difficult for hackers to trace back your online activities to your device.
Reinforcing Device Defenses
Protecting our personal data from hackers is a top priority in today’s digital age. With cyberattacks becoming increasingly sophisticated, it is essential to reinforce the defenses of our devices. By adopting best practices for robust password management, utilizing anti-virus software and firewalls, and educating users on recognizing and avoiding security threats, we can significantly reduce the risk of our personal data being stolen.
Best Practices For Robust Password Management
One of the simplest yet most effective ways to reinforce device defenses is through robust password management. Using strong and unique passwords for each online account is crucial. Here are some best practices to follow:
- Create passwords that are at least 12 characters long and include a combination of uppercase and lowercase letters, numbers, and special characters.
- Avoid using easily guessable personal information, such as your name, birthdate, or phone number, as part of your passwords.
- Regularly change your passwords to minimize the risk of unauthorized access.
- Consider using a password manager to securely store and generate complex passwords.
The Critical Role Of Anti-virus Software And Firewalls
Installing reliable anti-virus software and firewalls on our devices is essential for protecting against malware, viruses, and other malicious threats. These security tools play a critical role in reinforcing our device defenses. Here are some key points to consider:
- Choose a reputable anti-virus software that offers real-time scanning and automatic updates.
- Regularly scan your device for viruses and malware to ensure early detection and removal.
- Enable firewalls to monitor incoming and outgoing network traffic, providing an additional layer of protection against unauthorized access.
- Keep your anti-virus software and firewalls up to date to ensure you have the latest security patches.
Educating Users On Recognizing And Avoiding Security Threats
While having robust password management practices and security tools is essential, educating users on recognizing and avoiding security threats is equally important. By raising awareness and providing guidance, we can empower users to protect their personal data. Here are some key steps to take:
- Train users to identify phishing emails, malicious websites, and suspicious links.
- Advise them not to share sensitive information with unverified sources or over unsecured networks.
- Encourage regular software updates for both operating systems and applications to patch any potential vulnerabilities.
- Remind users to be cautious when downloading and installing software or apps from unofficial sources.
In conclusion, reinforcing device defenses is crucial in safeguarding our personal data from hackers. By adopting best practices for password management, utilizing anti-virus software and firewalls, and educating users, we can minimize the risk of falling victim to cyberattacks. Protecting our personal information should always be a priority to ensure a safe and secure digital experience.
Frequently Asked Questions Of How Do Hackers Steal Personal Data From Our Devices?
How Do Hackers Steal Your Data?
Hackers steal your data through phishing attacks, where they pretend to be a trusted source and trick you into sharing sensitive information like passwords. They can also use malware or malicious code to gain access to your device. Additionally, hackers may manipulate you through social engineering tactics or set up fake Wi-Fi networks to steal your personal information.
How Do Hackers Get Into Your Device?
Hackers can get into your device through phishing attacks, where they pretend to be a trusted entity and trick you into revealing sensitive information. They can also use malware, malicious code, or exploit security vulnerabilities to gain access. Jailbroken or rooted devices are especially vulnerable to hacking.
It’s important to be cautious and use security measures to protect your device.
What Is The Most Common Method That Hackers Use To Get Access To Your Personal Data?
Hackers commonly use phishing scams to steal personal data, such as passwords. They pretend to be legitimate entities, like banks, and request sensitive information through emails or other electronic communications. Another method is using malware to steal credentials.
Which Method Do Hackers Use To Steal The Information From A Computer?
Hackers use various techniques to steal information from a computer, such as phishing, fake WAPs (Wireless Access Points), waterhole attacks, brute forcing, bait & switch, and clickjacking. They may also create malicious apps or set up fake public Wi-Fi networks to trick users into sharing their personal information.
Conclusion
To protect our personal data from hackers, it is important to be aware of their tactics. Hackers often employ phishing scams, where they pretend to be a trusted entity to trick us into giving up sensitive information. They can also use malicious apps or take advantage of vulnerabilities in our devices.
It is crucial to stay vigilant, avoid clicking on suspicious links or downloading unknown apps, and regularly update our devices’ security features. By taking these precautions, we can safeguard our personal information from falling into the wrong hands.