Social engineering scams trick people into giving away personal information or money by exploiting trust. These scams are increasingly common, with 2024 data showing consumers lost over $12.5 billion to fraud, a 25% increase from the previous year. Below, we break down the most common types and their impact.
Common Types
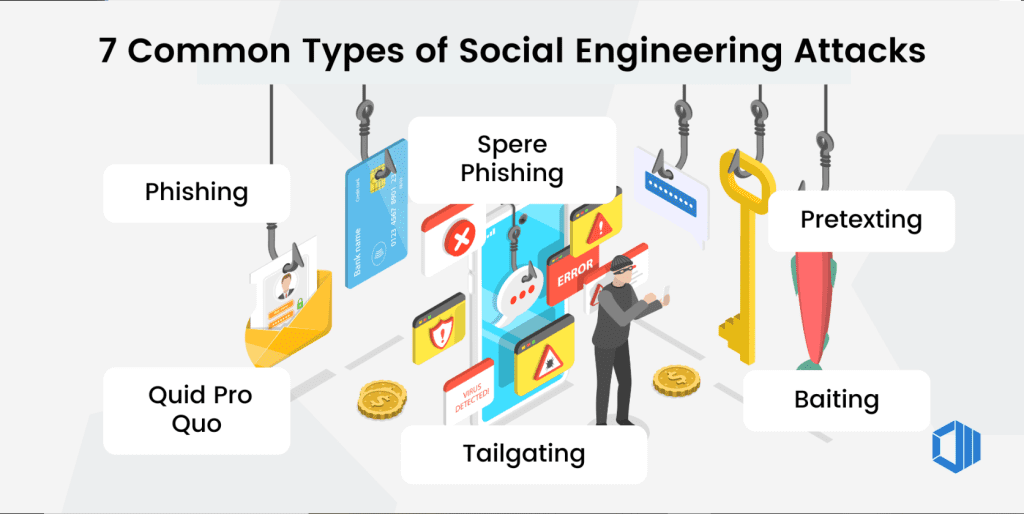
Social engineering scams manipulate people into revealing sensitive information, making security mistakes, or giving access to restricted systems. Here are some of the most common ones:
- Phishing
Scammers send deceptive emails, texts, or create fake websites to steal sensitive information like passwords or credit card details. This includes spear phishing, targeting specific individuals, and smishing, using text messages. - Vishing
Voice phishing involves scammers making urgent phone calls, often pretending to be from banks or government agencies, to extract information or money. - Pretexting
Scammers create false scenarios, like posing as a bank representative, to trick victims into sharing details. - Imposter Scams
A broad category where scammers impersonate trusted entities, such as government officials or tech support, leading to high reported losses, especially in government imposter scams at $789 million in 2024. - Baiting
Offering something enticing (e.g., free downloads, USB drives left in public places) to lure users into compromising their security. - Quid Pro Quo
Scammers offer a service or benefit (like free tech support) in exchange for sensitive information or system access. - Tailgating (Piggybacking)
Gaining physical access to restricted areas by following authorized personnel without proper authentication. - Watering Hole Attacks
Cybercriminals infect websites frequently visited by a specific group (e.g., employees of a company) to spread malware. - Dumpster Diving
Searching through trash bins to retrieve sensitive information like passwords, account details, or company documents. - SIM Swapping
Attackers convince mobile carriers to transfer a victim’s phone number to a new SIM card, allowing them to bypass SMS-based authentication.
Unexpected Detail
While phishing is widely known, the rise in job-related scams, with reports tripling since 2020 and losses up to $501 million in 2024 for job/employment agency scams, highlights a growing threat in professional contexts.
Facts of Social Engineering Scams
Social engineering scams leverage psychological manipulation to deceive individuals into divulging confidential information or performing actions that benefit the scammer. These scams do not rely on technical hacking but on exploiting human trust, making them a pervasive threat. According to the Federal Trade Commission (FTC), consumers reported losing over $12.5 billion to fraud in 2024, a 25% increase from 2023, driven by a higher percentage of victims losing money rather than an increase in reports alone New FTC Data Show a Big Jump in Reported Losses to Fraud to $12.5 Billion in 2024. This surge underscores the evolving nature of these scams, with email, phone calls, and text messages being the most common contact methods.
Most Common Social Engineering Scams
Based on 2024 FTC data and cybersecurity reports, the following scams are identified as most common, ranked by frequency of reports and financial impact:
| Scam Type | Description | Reported Losses (2024) | Notes |
| Imposter Scams | Scammers pretend to be trusted entities like government officials, banks, or tech support, often using urgent tactics. | $2.95 billion total, $789 million for government imposters | Most commonly reported category, with government imposter losses up $171 million from 2023. |
| Phishing | Deceptive emails, texts (smishing), or websites to steal sensitive information, including spear phishing targeting individuals. | Not specified separately, but email is the top contact method. | Pervasive, with 98% of cyberattacks involving some form of social engineering per 2021 reports. |
| Vishing | Voice phishing, using phone calls to create urgency, often impersonating banks or law enforcement. | Included in imposter scams, significant impact. | Common, especially in urgent voicemail scenarios. |
| Pretexting | Creating false scenarios, like posing as a bank representative, to extract information. | Included in imposter scams, notable in organizational targets. | Leveraged against entities with client data, high success rate. |
| Business and Job Scams | Includes job/employment agency scams, where scammers promise jobs or business opportunities, often requiring upfront payments. | $750.6 million total, $501 million for job/employment agency scams. | Reports tripled since 2020, losses up from $90 million in 2020, reflecting a growing trend. |
| Investment Scam | Promising high returns, often involving baiting or quid pro quo tactics, leading to significant losses. | $5.7 billion, up 24% from 2023. | Fourth most reported, highest loss category, often overlapping with social engineering tactics. |
This table integrates data from the FTC report, which highlights imposter scams as most reported and investment scams as highest in losses, with additional details from cybersecurity sources like Terranova Security, which lists nine common types including baiting and water-holing 9 Examples of Social Engineering Attacks.
Breakdown of Each Scam
Phishing
This is the broadest category, encompassing email phishing, smishing (text messages), and spear phishing, which targets specific individuals with tailored messages. It remains the most pervasive due to its scalability, with email being the top contact method in 2024 FTC data. For example, scammers might send emails pretending to be from Amazon, asking users to verify account details, leading to data theft.
Vishing
Voice-based scams, often involving urgent voicemails from supposed banks or government agencies, convince victims to act quickly, such as providing bank details to avoid arrest. This is a subset of imposter scams, with significant reported losses in the FTC data.
Pretexting
Scammers create fabricated scenarios, like claiming to be from IT support, to extract information. This is particularly effective against organizations, as seen in cases targeting banks, and is part of the imposter scam category.
Imposter Scams
This broad category includes government imposter scams, where scammers pose as IRS officials, and tech support scams, claiming computer issues. The FTC reports $789 million in losses for government imposters in 2024, up from previous years, reflecting its prevalence.
Business and Job Scams
A growing trend, especially with remote work, these scams involve fake job offers requiring upfront payments or personal information. The FTC notes job/employment agency scams at $501 million in losses, with reports tripling since 2020, highlighting a shift in scammer focus to professional contexts.
Investment Scams
Often involving baiting (promising rewards) or quid pro quo (offering services for information), these scams saw $5.7 billion in losses in 2024, up 24% from 2023. They overlap with social engineering, using emotional manipulation like fear or greed.
Trends and Insights
The 2024 data reveals a shift toward more sophisticated tactics, with imposter scams and job-related scams gaining traction. Email remains the primary vector, followed by phone calls and texts, aligning with phishing and vishing prevalence. The increase in job scams, with losses up nearly $250 million from 2023, is an unexpected detail, reflecting scammers exploiting economic uncertainties and remote work trends. This is particularly relevant as of April 2025, with cybersecurity reports continuing to track these trends.
The FTC’s 2024 report provides detailed statistics, showing imposter scams as most reported and investment scams as highest in losses, with interactive dashboards for further exploration at ftc.gov/exploredata. Terranova Security’s list of nine common attacks, including phishing, vishing, and pretexting, corroborates these findings, offering examples like malware-infected USBs for baiting 9 Examples of Social Engineering Attacks. Mastercard’s 2025 article also notes imposter scams as most reported, with email and phone as top methods, aligning with FTC data Your guide to identifying social engineering scams and cyber threats.
How to Protect Yourself from common social engineering scams?
Protect Against Phishing (Emails, Calls, SMS)
✅ Verify Sources: If you receive an email or message asking for sensitive info, call the company directly using an official number.
✅ Look for Red Flags: Poor grammar, urgent language, and unfamiliar senders are signs of phishing.
✅ Check Links Before Clicking: Hover over links to see where they lead before clicking.
✅ Use Email Filters: Many email services automatically detect and filter phishing emails.
✅ Enable Multi-Factor Authentication (MFA): This adds an extra layer of security even if your credentials are stolen.
Stay Safe from Pretexting Scams
✅ Never Share Personal Info Over Calls/Emails: Banks and government agencies won’t ask for sensitive details via phone or email.
✅ Ask Questions: If someone claims to be from IT or HR, ask specific questions to verify their legitimacy.
Prevent Baiting Attacks
✅ Avoid Using Unknown USB Drives: Never plug in an unfamiliar USB drive you find in public.
✅ Download Software Only from Trusted Sources: Avoid free or pirated software from unknown sites.
Stop Quid Pro Quo Attacks
✅ Be Skeptical of Free Offers: If someone offers free services in exchange for login credentials or access, it’s likely a scam.
✅ Verify IT Support Calls: If someone claims to be from tech support, contact your official IT department first.
Protect Against Tailgating & Impersonation
✅ Don’t Hold Doors Open for Strangers: At offices, only allow authorized individuals to enter secure areas.
✅ Always Check Employee IDs: Verify the identity of service personnel before granting access.
Prevent Business Email Compromise (BEC) & CEO Fraud
✅ Verify Financial Transactions: Before transferring funds, confirm requests through a phone call to a known number.
✅ Use Company-Approved Email Accounts: Avoid using personal email for work-related financial transactions.
Social Media & Romance Scam Prevention
✅ Limit Sharing Personal Info: Don’t post sensitive details like your full birthday, location, or travel plans.
✅ Be Cautious of Online Friends: If someone you met online quickly asks for money or personal details, it’s a scam.
✅ Set Your Profiles to Private: Prevent strangers from accessing your personal information.
Avoid SIM Swapping & Account Takeovers
✅ Enable a PIN or Passcode with Your Carrier: This prevents unauthorized SIM changes.
✅ Use App-Based Authentication Instead of SMS: Authenticator apps (Google Authenticator, Authy) provide more security than SMS-based verification.
Stop Watering Hole Attacks & Malware Infections
✅ Update Your Software & Browsers Regularly: Prevent attackers from exploiting vulnerabilities.
✅ Use a Reputable Antivirus: Protects against malware from infected sites.
Secure Your Trash & Data
✅ Shred Important Documents: Avoid dumpster diving attacks.
✅ Secure Old Devices Before Disposing: Wipe hard drives and factory reset phones before selling or recycling.
Conclusion
In summary, phishing, vishing, pretexting, and imposter scams are the most common social engineering scams in 2024, driven by their frequency and financial impact. The rise in job-related scams adds a new dimension, reflecting evolving scammer strategies. This analysis, based on recent FTC and cybersecurity reports, provides a comprehensive view as of April 2025, highlighting the need for awareness and education to mitigate these threats.