Cybersecurity focuses on protecting electronic systems and data from cyber threats, while information security is a broader term encompassing the protection of information in any form from unauthorized access, use, or disclosure. Understanding the nuances between cybersecurity and information security is crucial for effective protection strategies in our increasingly digital world.
With our daily lives interwoven with digital transactions and communications, recognizing the distinct roles of cybersecurity and information security becomes essential. Cybersecurity is the armory that guards our internet-connected systems against cyber-attacks, be it malware, phishing, or other forms of exploitation.
Contrarily, information security is an umbrella term that not only secures data from cyber threats but also includes physical and administrative measures to safeguard information integrity and confidentiality, regardless of its form. Both areas are vital parts of a comprehensive security strategy, ensuring that our personal, financial, and business information remains out of the reach of unauthorized individuals. This integral knowledge forms the foundation to avert potential breaches and fortify our digital and physical informational assets.
Cyber Security Vs. Information Security: Short Overview
In our digital world, protecting our data is more important than ever. Two terms often come up: cyber security and information security. But what do they mean, and how are they different? This blog post will dive deep into the world of data protection, exploring the key concepts within cyber security and information security. We will also discover why keeping our digital lives secure is critical in today’s tech-savvy era.
Key Concepts In Data Protection
Cyber security focuses on defending our computers, servers, and networks from digital attacks. Information security, on the other hand, is all about protecting data from any form of threat, whether digital or physical. Both areas share a common goal: safeguarding our information. Below are the pillars that hold them:
- Confidentiality: Ensuring only authorized people can see the data.
- Integrity: Keeping our information accurate and complete.
- Availability: Making sure data is there when needed.
The Significance Of Security In The Digital Age
As we move more of our lives online, security becomes vital. Cyber attacks can lead to stolen identities, lost money, and ruined reputations. Information breaches can expose sensitive data, causing harm to individuals and companies alike. Here are reasons why staying secure is non-negotiable:
| Reason | Description |
|---|---|
| Personal Protection | Keeps your private life and data away from prying eyes. |
| Financial Security | Guards against fraud and theft that could cost you. |
| Company Reputation | Ensures businesses maintain trust and avoid legal problems. |
Digging Deep Into Cyber Security
Exploring cyber security means stepping into a world filled with digital shields and battlegrounds. It is a vital part of protecting our online presence. This goes beyond simple firewalls and antivirus programs. Let’s unlock the secrets of this digital armor and understand how it keeps our treasured information out of the wrong hands.
The Domain Of Cyber Threats And Defense
Cyber threats loom everywhere in the online world. Think of them as invisible thieves ready to steal your digital gold. But fear not, as cyber security is the knight in shining armor, guarding against these threats. From nasty viruses to clever hackers, the internet is a playground for danger. Let’s break down the types of threats and the shields used to defend against them.
- Malware: Software designed to harm your devices.
- Phishing: Fake emails trick you into giving away private info.
- Ransomware: Locks your files unless you pay a ransom.
- Spyware: Sneaks into your device to spy on actions and steal data.
Tools And Techniques In Cyber Security
Like a skilled warrior, cyber security uses an arsenal to protect against threats. Each tool, each technique, has its purpose. They work together to create a fortress around your data. Let’s peek into the toolkit that keeps these cyber guardians at the top of their game.
| Tool/Technique | Use |
|---|---|
| Firewalls | Blocks unauthorized access |
| Encryption | Scrambles data to hide information |
| Antivirus Software | Finds and removes harmful software |
| Two-Factor Authentication | Adds an extra security layer for access |
Each piece of this toolkit not only defends but also helps in detecting and responding to cyber attacks promptly. Together, they form a robust strategy that adapts to emerging threats, ensuring our virtual walls remain unbreached.
Exploring The Domain Of Information Security
At its core, information security stands as a fortress guarding crucial data. It concerns protecting digital and analog information from unauthorized access, disclosure, or theft. Unlike cyber security, which focuses on digital spaces, information security is broader. It involves physical and digital measures to secure data, ensuring confidentiality, integrity, and availability.
Principles Of Safeguarding Information
In the realm of information security, three cornerstone principles set the foundation. They form a model known as the CIA triad:
- Confidentiality: Only the right eyes see sensitive information.
- Integrity: Data remains unchanged unless by authorized hands.
- Availability: Information is ready for use when needed.
These principles act as a guide in creating secure systems. Every measure employed circles back to one or more of these ideals.
Methods Of Ensuring Data Privacy And Integrity
Keeping data safe and unaltered is critical. Various strategies exist to achieve this:
| Method | Description |
|---|---|
| Encryption | Transforms data into a secret code, hiding its contents. |
| Access Controls | Limits who can view or use the data. |
| Data Backup | Creates copies to prevent loss. |
| Data Masking | Hides specific areas of data. |
Employing these methods ensures the CIA triad stands strong against threats.
Comparing Two Critical Fields
In the sense of digital defense, two vital fields emerge: Cybersecurity and Information Security. While they share common goals, it’s crucial to distinguish between them. Understanding these differences ensures stronger protection strategies in the ever-evolving threat landscape.
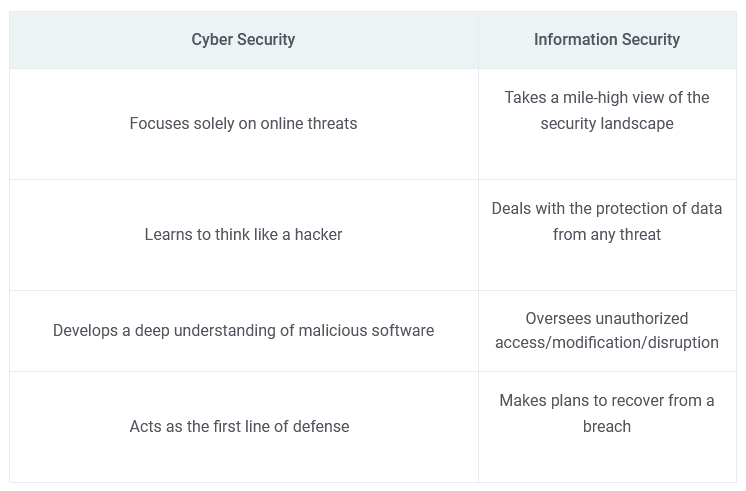
Contrast In Objectives And Methods
Cybersecurity focuses on protecting electronic data from cyber threats. It deals with the defense of computer systems, networks, and data processed online. Information Security, on the other hand, safeguards all information forms. Its umbrella covers both digital and physical data security.
| Cybersecurity | Information Security |
|---|---|
| Protects against internet-based threats. | Secures data integrity, confidentiality, and availability. |
| Employs firewalls, antivirus, and intrusion detection systems. | Uses encryption, access control, and classification. |
The Overlap Between Cyber And Information Security
Despite their differences, a significant overlap exists. Both aim to protect valuable data. The two fields often work hand-in-hand to provide a comprehensive security approach.
- Risk Management: Identifying and mitigating risks is central to both.
- Security Policies: Implementing strict guidelines to safeguard data.
- Breach Response: Quick action is essential when a breach occurs.
The Impact On Business And Individual Practices
Businesses and individuals rely on digital platforms for various tasks. Protecting data from threats is vital. Cybersecurity and information security both aim to safeguard data. They affect how firms shield secrets and how people keep personal info safe. Firms must understand the differences to pick the right defense plans.
Choosing the right security measures
Choosing The Right Security Measures
Businesses must choose suitable security measures to safeguard assets. It starts with knowing what to protect. Cyber threats can attack systems; information security shields data from any kind of harm.
| Type of Protection | Cyber Security | Information Security |
|---|---|---|
| Focus | Defends against cyber attacks | Keeps all info safe |
| Tools | Firewalls, Antivirus software | Data encryption, Access controls |
Identify threats and match tools to your needs. It is crucial for a sturdy defense.
Adopting best practices for protection
Adopting Best Practices For Protection
Beyond picking Security measures, adopting best practices is key. This ensures data stays secure at all times. Uncover and apply standards to your routines.
- Regularly update software to fend off risks.
- Train employees on security policies.
- Use strong passwords and change them often.
- Back up data to recover from data loss.
Stay vigilant against new threats. Regular security audits help reveal weaknesses. Patches and updates are your digital armor. Ensure they are in place.
/AL_14-Blog02-4.jpg?width=450&height=450&name=AL_14-Blog02-4.jpg)
Frequently Asked Questions
Which Is Better Cybersecurity Or Information Security?
Neither cybersecurity nor information security is universally better; the choice depends on specific career goals. Cybersecurity focuses on protecting against cyber attacks, while information security encompasses overall data protection strategies. Your interests and professional needs will determine the best fit.
Is There A Difference Between It And Cyber Security?
Yes, IT generally encompasses all forms of technology management, while cybersecurity focuses specifically on protecting systems and data from digital attacks.
What Is The Difference Between It Security And Information Security?
IT security specifically protects physical and digital data assets from cyber threats. Information security broadly safeguards all data, whether electronic or physical, from unauthorized access.
What Is An Example Of Information Security?
An example of information security is using encryption to protect data during online transactions. This ensures that sensitive information, like credit card numbers, remains confidential.
Conclusion
Understanding the nuances between cyber security and information security is pivotal. While both fields aim to protect data across digital and physical spectrums, their strategies differ. Cybersecurity focuses on defending electronic data from cyber threats, whereas information security encompasses a broader scope, protecting both digital and analog information.
Recognizing their distinct roles empowers organizations to better safeguard their assets. Embrace their synergies for a robust security posture.