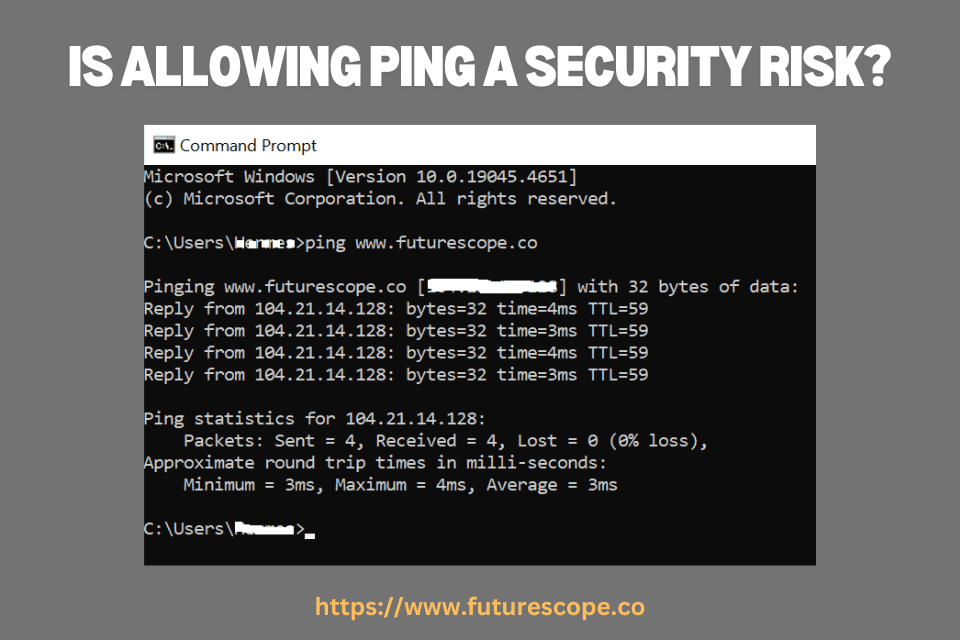
Allowing ping can be a security risk as it may expose network visibility to attackers. It allows them to map your network infrastructure.
Ping, a network utility tool, verifies the reachability of a host on an Internet Protocol (IP) network and measures the round-trip time for messages sent. Despite its usefulness for network diagnostics, ping can provide attackers with the information needed to target a network.
The ping command, which uses the Internet Control Message Protocol (ICMP), is a standard network utility that helps determine whether a particular host is reachable and how long packets take to travel. While it’s essential for network diagnostics, allowing ping requests (ICMP Echo Requests) on public networks may pose potential security concerns.
Security-conscious administrators often consider the management of ICMP (Internet Control Message Protocol) requests to mitigate potential threats. They evaluate the trade-off between useful network insights and the exposure to reconnaissance activities by potential attackers. Ensuring that network monitoring practices are balanced with security measures is imperative for maintaining the integrity of any IT infrastructure.
This article explores whether enabling ping is a threat, how attackers might misuse it, and best practices for securing your network.
The Function of Ping In Network Diagnostics
Picture you’re shouting in a canyon, waiting for an echo. In the digital world, that’s ping. It’s a tool that helps find and fix network problems. Let’s explore how ping keeps our online conversations smooth.
What is Ping and How Does It Work?
The ping command is a basic diagnostic tool used to test the availability and responsiveness of devices on a network. It sends an ICMP Echo Request to a target IP address, and if the target is reachable, it replies with an ICMP Echo Reply. This test measures two things. First, can the target be reached? Second, how long does the message take to travel? This method is incredibly useful for troubleshooting network connectivity issues, checking server status, and measuring round-trip time.
Echo requests and replies are like digital handshakes. If they’re fast and successful, your network is in good shape.
Utilizing Ping For Troubleshooting
When a website won’t load or an email fails to send, ping is a go-to tool. By running a simple command, you can check the connection between your device and another location. Here’s how to use ping:
- Open your command prompt or terminal.
- Type
pingfollowed by the IP address or web address. - Press enter and observe the results.
If ping returns a series of replies, your connection to the target is working. No replies? There might be a blockage or the target might be down. Ping’s results can help pinpoint where the problem lies — is it on your end, your internet service provider’s network, or the website you’re trying to reach?
Ping is a simple but powerful tool for network troubleshooting. It’s like having a trusty flashlight in the dark corners of the web. Remember to use ping wisely.
Why Allowing Ping Can Be a Security Concern?
While ping is a helpful tool, allowing ping requests from external networks can introduce vulnerabilities:
Potential Security Risks of Ping
Understanding the security risks of ping is vital for protecting a network. The ping utility is a common tool for troubleshooting network issues. It checks if a machine can receive requests from other systems. While helpful, it may expose a network to risks.
Ping And Reconnaissance Attacks
Ping can become a tool for cyber attackers. Hackers often use ping sweeps or ICMP scans to discover live hosts in a network. If a server responds to ping, it confirms that the IP is active and online, which may encourage attackers to probe further for vulnerabilities.
This process is scanning or reconnaissance. It is the first step in finding potential targets. By allowing ping, you might give hackers a map of your network’s devices.
Denial Of Service (DoS) Vulnerability
In distributed Denial of Service (DoS) attacks, ICMP can be misused to flood a system with requests (This can slow down or crash the device or network. It is called a Ping Flood attack.), exhausting its bandwidth or resources. Though modern firewalls help mitigate this, some networks are still vulnerable if ICMP isn’t properly configured
More To read > > > Why is My Ping So High All of a Sudden?
Safeguarding Against Ping-based Threats
Protecting your network from unwanted pings is like keeping your home safe from strangers. Ping can be a useful tool for checking if devices are online. Yet, it can also open doors for hackers. Let’s make sure only friends, not foes, can give us a ping!
Firewall Configurations To Block Ping
Your firewall is like a gatekeeper. It can stop ping messages that may cause harm. Setting it up right is key. Here’s how you can adjust it to keep your network safe:
- Access your firewall settings: Find where to change rules.
- Create a rule: Make one that says
Noto ping requests. - Apply it to all incoming traffic: This blocks pings from outside.
- Save changes: Lock in your new safety rule.
Remember, some pings are okay. You can allow them inside your local network.
Network Monitoring For Suspicious Ping Activity
Watching your network is like being a detective. You look for clues that something’s wrong. An odd ping could be a sign. Here are ways to catch them:
- Use tools: Tools can keep an eye on pings for you.
- Check logs: Logs show you who tried to ping.
- Set alerts: Get told when there’s a strange ping.
- Act fast: If you see a weird ping, check it out at once.
Staying alert makes sure you spot threats before they get in.
Balancing Accessibility With Security
Balancing accessibility with security often feels like a high-wire act. Picture an Internet Protocol (IP) network as a bustling city. Just as city planners use signals to manage traffic flow, network administrators use Internet Control Message Protocol (ICMP) echo requests, commonly known as “ping”, to manage network connectivity. Whether to allow ping responses on a network can provoke debate: should doors be open to signal availability or closed to guard against prying eyes?
When To Allow Ping Responses?
Deciding when to permit ping responses involves measuring the benefit against the potential risks. Pinging can be harmless and useful for network diagnostics. Here are scenarios where enabling ping is beneficial:
- Network Troubleshooting: Quickly verify if devices are reachable.
- Server Monitoring: Use pings to check the health of servers.
- User Support: Aid support teams in resolving connectivity issues.
However, ping responses can also attract unwanted attention from attackers seeking network vulnerabilities. Therefore, it may be wise to disable them:
- In High-Security Zones: Where data sensitivity is paramount.
- On Exposed Devices: Public-facing devices can avoid revealing their presence.
Best Practices for Allowing Ping in Firewall Rules
To balance the benefits and risks, follow these best practices for configuring ICMP in firewall rules:
| Best Practice | Description |
|---|---|
| Allow Specific ICMP Types | Permit only necessary ICMP types, such as Type 0 (Echo Reply), Type 3 (Destination Unreachable), Type 8 (Echo Request, with throttling), and Type 11 (Time Exceeded) to support diagnostics and PMTUD (Reddit ICMP Discussion). |
| Rate Limiting | Implement throttling (e.g., 2 pings/second, burst of 5) to prevent resource exhaustion from ping floods (Should I Block ICMP?). |
| Restrict by Network Context | Allow ping freely in internal networks for troubleshooting but restrict it from untrusted external sources, especially for sensitive systems (Ciscopress Best Practices). |
| Stateful Inspection | Use firewalls with ICMP stateful inspection to ensure replies match requests, reducing the risk of abuse (Cisco Firewall Best Practices). |
| Avoid Broad Rules | Do not use “permit icmp any any” rules, as they expose the network to unnecessary risks. Use specific access control lists (ACLs) (Cisco Firewall Best Practices). |
| Proxy Firewalls | Use proxy firewalls to filter ICMP traffic, allowing only necessary messages (Reddit ICMP Discussion). |
Implementing A Secure Ping Policy
Establishing a secure ping policy safeguards data while keeping certain doors open. Here’s a step-by-step guide:
| Step | Action | Purpose |
|---|---|---|
| 1 | Analyze network topology. | Identify critical segments where ping should be restricted. |
| 2 | Implement firewalls. | Control incoming and outgoing traffic based on pre-defined security rules. |
| 3 | Configure selective accessibility. | Permit ping only from trusted sources and to non-sensitive areas. |
| 4 | Monitor and audit. | Review logs to detect anomalous activity or unauthorized ping attempts. |
Remember, a policy must be dynamic. Modify it as threats evolve and new security practices emerge. Ensuring the network remains responsive yet secure is the goal. Imprint this mantra: accessibility does not have to mean vulnerability.
Best Practices for Secure ICMP Configuration
To reduce security risks while still benefiting from ICMP functionality, consider these best practices:
- Use firewalls to control ICMP traffic, especially for internet-facing devices.
- Allow ICMP only from trusted IP ranges (e.g., internal subnets or admin workstations).
- Rate-limit ICMP requests to prevent flooding or abuse.
- Monitor ICMP traffic logs for unusual patterns or spikes.
- Disable ping responses on critical public infrastructure, unless needed for specific monitoring purposes.
Frequently Asked Questions
Why Is Ping A Security Risk?
Ping can expose a network to security risks by enabling reconnaissance attacks where malicious actors discover and map systems for vulnerabilities.
Should I Allow Pings?
Allowing pings on your website can help notify other sites about updates, potentially increasing visibility and backlink growth. Consider privacy and spam risks before enabling them.
How Allowing ICMP Messages Could Be Considered A Security Risk?
Allowing ICMP messages can expose networks to ping floods, ICMP tunneling, and reveal network topology, creating a potential vulnerability for cyberattacks.
More to read > > > Why Does My Ping Fluctuate?
Why Is ICMP Viewed As Posing A Security Risk?
ICMP can pose security risks due to its potential for misuse in network attacks like Denial of Service (DoS) and ping sweeps, which can lead to system overloads and unauthorized access to network information.
Should You Block or Allow Ping?
Whether to block or allow ping depends on your use case:
- For public-facing servers (like web servers): It’s generally advisable to disable ICMP Echo Requests to reduce the server’s visibility and attack surface.
- For internal networks and troubleshooting: You may want to enable ping for diagnostics, especially within a controlled environment.
- On firewalls and routers: Many security experts recommend configuring ICMP responses more granularly—rate-limiting, logging, or allowing only internal ICMP traffic.
Does Blocking ICMP Improve Security?
Blocking all ICMP traffic is not recommended, as it can disrupt network functionality and troubleshooting without significantly enhancing security. Selective filtering is a better approach (Paessler Blog).
Can Ping Be Used to Harm My Network?
While ping can be used in attacks like floods or reconnaissance, these risks can be mitigated with rate limiting and source restrictions. Modern systems are also resistant to older vulnerabilities like the ping of death (Cloudflare ICMP Overview).
Should I Allow Ping on Public Servers?
For public-facing servers, consider allowing ping only from trusted sources or for specific purposes (e.g., diagnostics). Ensure rate limiting and stateful inspection are in place to minimize risks (Ciscopress Best Practices).
Conclusion
Understanding the balance between functionality and security is crucial for network administrators. Allowing ping can be a double-edged sword, potentially exposing systems to unnecessary risk. It’s essential to evaluate your security needs and configure your network accordingly. Secure practices and vigilant monitoring are key to mitigating security concerns associated with ping.